Should You Use Two-Factor Authentication
 |
| Should You Use Two-Factor Authentication |
What precisely is two-factor validation and what begun it? Two-Factor Authentication happens when you are required to utilize two kinds of ID to sign into a site or open your email. It was begun on the grounds that individuals were utilizing powerless passwords or no passwords by any stretch of the imagination.
Typically the principal factor is a secret key. As an update, your passwords should utilize numbers, capital and little letters and images. They ought not be any kind of lexicon word and be at any rate 12 characters in length, the more drawn out the better. You ought to never reuse a secret phrase. Whenever utilized effectively, you will require a secret key administrator to recollect them all. Getting one it is well justified, despite all the trouble.
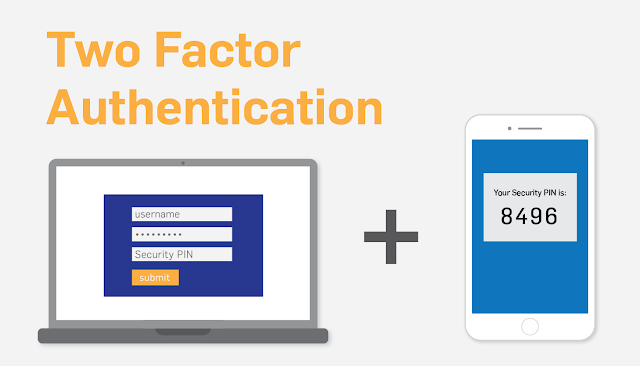
The second factor can fluctuate generally from unique finger impression or facial acknowledgment to the site sending you a numeric code by means of content or email that you should go into their site as a major aspect of the sign in procedure. Google, Microsoft and others are taking a shot at different strategies for verification that will be secure and make it simpler for the end client.
The best kind of security is the one that individuals will utilize. Two-Factor Authentication takes somewhat longer to sign into a site, it will include 15-30 seconds. That time would be time all around spent to ensure your security. Sites; particularly banks, budgetary and medicinal services locales, need to make sure that when a client signs in it is in certainty the right individual. This is hard to do with only a secret phrase. Consider every one of the passwords stolen a year ago because of programmers.
This is the place your telephone is utilized to affirm your character. Let's assume you sign into your bank's site. On the off chance that you utilize your telephone for that login, your unique finger impression or facial acknowledgment can be utilized to ID you. On the off chance that you utilize a personal computer, they will for the most part send a numeric code to your telephone that you use amid the login procedure. In either case you gave the bank your cell phone number, so they have probably some affirmation that it is you. You likewise enter your secret phrase that matches what the bank has on record. This is the means by which Two-Factor Authentication works, two sorts of distinguishing proof.
As I expressed before, sites and organizations are attempting to make this login procedure simpler and progressively secure. This is a difficult activity as simpler and increasingly secure don't generally cooperate.
